Security Patch is a piece of software designed to update a computer program or its supporting data for fixing as well as for improving its performance and security.
Magento is improving its security day-by-day by releasing its updated security patches: SUPEE-8788 is the new update for Magento 1. Released on Oct 11th, 2016, the update comes with several security improvements. You can download it from this download page.
On clicking the download page it will redirect you to the following page:
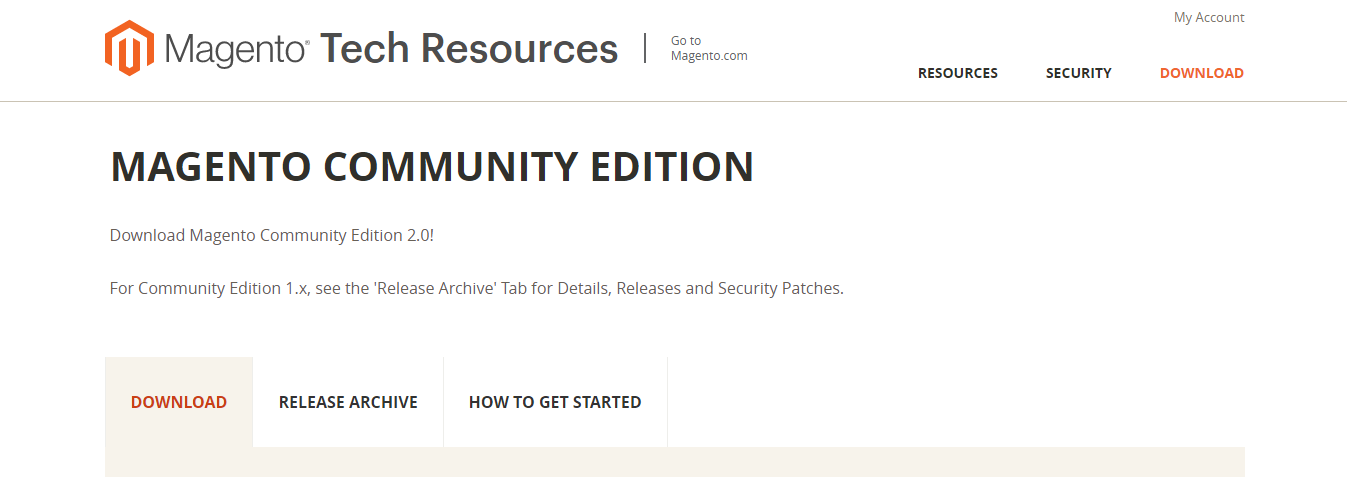
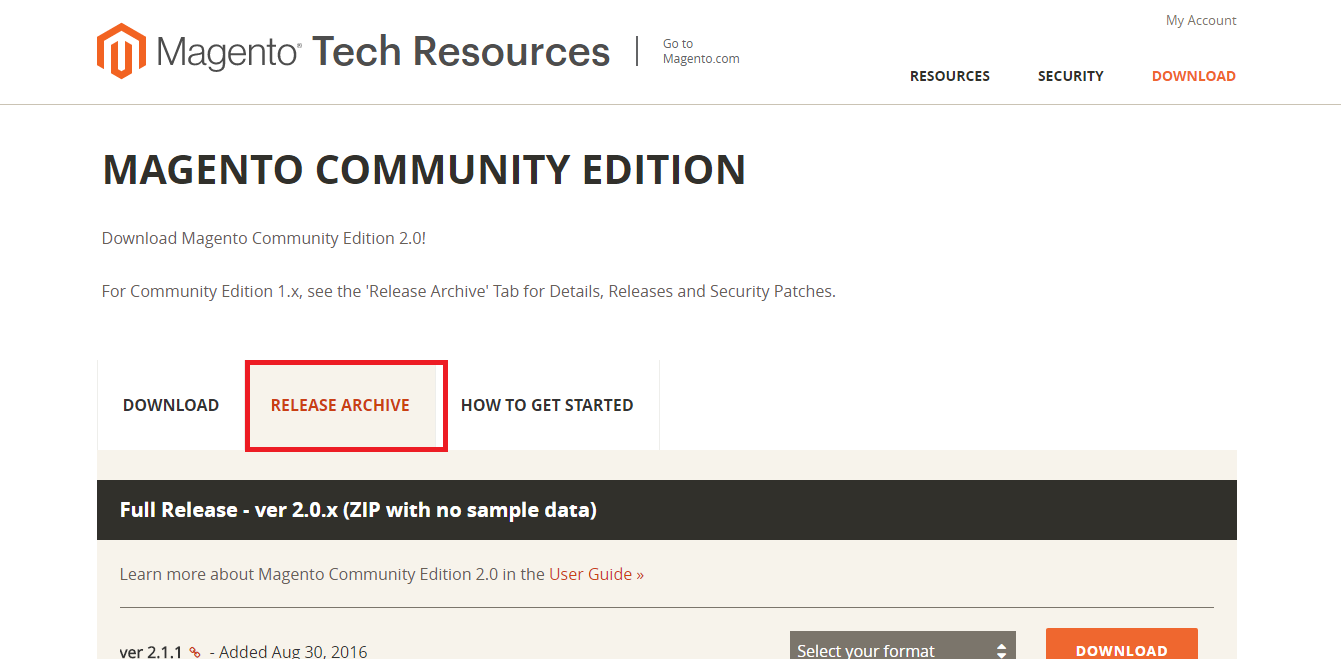
Navigate to the Release Archive tab:
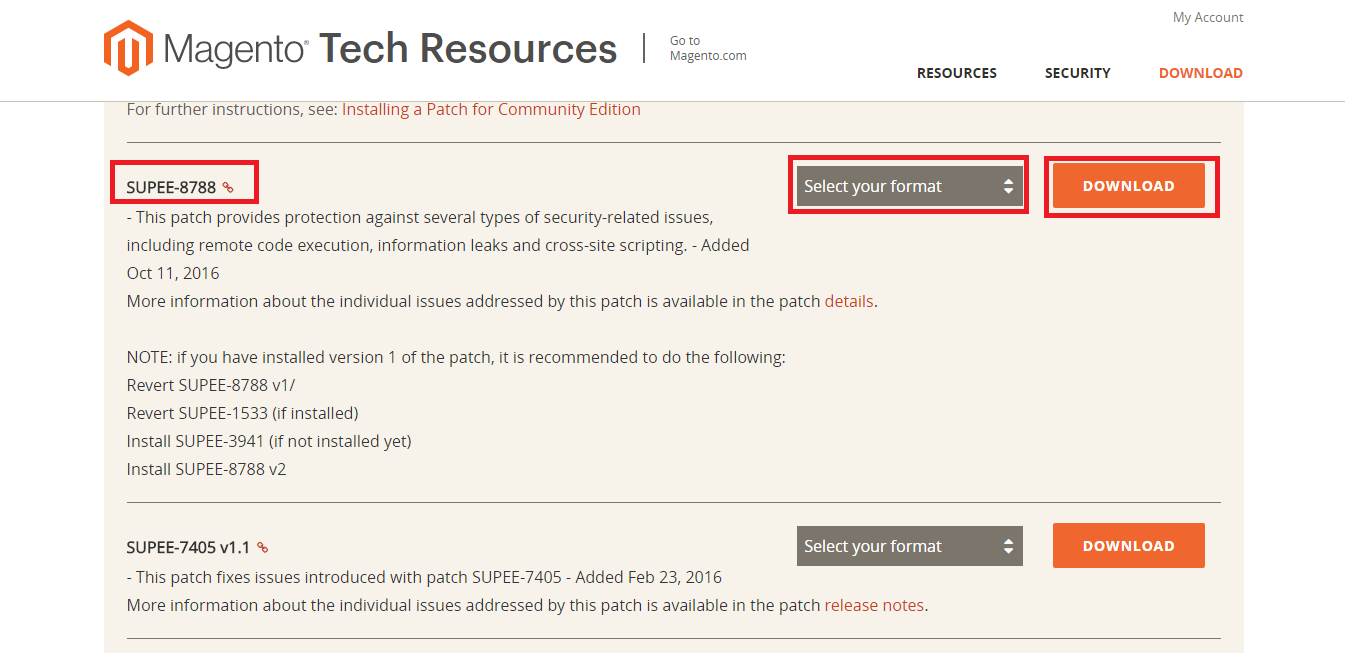
Now scroll down the page to find SUPEE-8788 security patch. In the Select Your Format menu, select your format and click Download.
Now, we are going to install SUPEE-8788:
- Upload the SUPEE-8788 patch file using a client like FileZilla to the Root Directory in Magento.
- Launch the SSH terminal and run this command:
patch -p0 < patch-file-name.patch for .patch file
sh patch_file_name.sh for .sh file
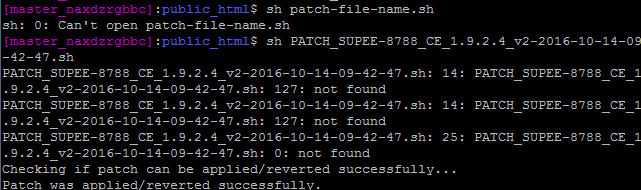
Troubleshooting
- Make sure that the patch is uploaded in the right directory, i.e., Magento Root Directory.
- Make sure that you are running the patch with sufficient rights in SSH control.
- Make sure that the commands you are applying are correct, i.e., file name, extension, etc.
- Try again with the same described method to install it.
- After successful installation, please check your patch with MageReport.
We recommend that our readers, Magento store owners, and all Magenticians readers in the Magento Community, install this updated security patch. SUPEE-8788 fixes Zend Framework and payment vulnerabilities, and also ensure that sessions are destroyed after a user logs out from the account. Many other security issues are resolved and addressed by SUPEE-8788 which are following:
- Malicious PHP code might be possible to execute with some payment method during checkout.
- A malicious user can inject SQL through the ordering and grouping parameters due to a bug in Zend Framework.
- By having access to any CMS functionality, an attacker with permission of administrator can use blocks to leak out the information that stored in the cache which includes store configuration, encryption key, and database connection details.
- It is possible in some configurations to log in as existing store customer while knowing only his email and not the password.
- In Magento unserialize data supplied from the admin dashboard without proper checks by using import/export functionality.
- To pass the data through URL is not a right approach as it is easily gettable for attackers. Magneto function that uses URL processing can lead to cross-site scripting issue.
- A malicious user can make a store temporarily down or interrupt services by uploading modified image (GIF) that can result in a script timeout. This attack called Denial of Services.
- Attackers can inject client-side scripts on those sites that use custom file option.
- Applying filters to the contact form or other admin features might not be enough to avoid Cross-Site Scripting.
- A malicious user can create a form through which state change request like transferring funds, changing emails and so on can be targeted when the user submits a form, and it is called Cross-Site Request Forgery (CSRF), and it is possible throughout Magento due to improper form key validations.
- When a user accesses the site by sharing his computer, then it is feasible to steal the session cookies, and also a user account can be accessible because sessions not expires after getting logout.
- Man-in-the-Middle can attack calls to external services due to lack of certificate validation. It can make it easy for the attacker to steal customer information and possibly change communication between two parties who are directly communicating with each other.
- By analyzing the time taken on password checking functionality, time attack can be executed which is theoretically possible.
Upgrade your Magento Store with security patch SUPEE-8788 to secure your store further. For further problems of security patch SUPEE-8788, see this thread.