
Disclaimer: Magenticians does not necessarily agree with the views expressed in this guest post. They are presented to bring to light all diverse views in the Magento and general ecommerce community.
For an ecommerce platform, Magento is second to none when it comes to usability and customization, but unfortunately, it is also prone to cyber fraud and security attacks. Magento is an open source and hosts more than 200k online stores, which includes the biggest ecommerce market, players. It is beyond question that even the slightest vulnerabilities spotted in the Magento code can be exploited. Hackers can devise more and more sophisticated brute force methods, and every store owner should ask himself: whether or not their store stand up to those threats.
Whatever the size of your business, you can totally afford a secure Magento configuration. This article is a guide about the best practices for Magento security, that can and must be implemented correctly before using any additional tools or extensions. Following this guide can save you a lot of time and effort in fixing issues that are easy to prevent.
Start Enforcing Now
Let’s begin with common knowledge: always use the latest version of Magento available. This fundamental yet elementary measure will ensure your installation is as secure as possible at the very moment.
Along with the latest Magento version, take instant notice of Magento security patches and install all of them. Every security patch is released to cover complex issues, including major vulnerabilities, new product compatibility issues, and smaller improvements. All the patches are important for your store’s safety, but there are a few you need to be exactly aware of:
- SUPEE-9767: The known security-related issue addressed by Magento developers in this patch was due to failed customer registration at checkouts. As a result, registered customers checked out as guests. To prevent this from happening to your customers, enable “Form Key Validation On Checkout” in System > Configuration > Admin > Security.
- SUPEE-6788: In this patch, a new option was added to admin security settings. It covered a vulnerability that allowed attackers to access the admin panel login page by calling a module directly via URL. This breach made it easier to perform password attacks. A new config option called ‘Admin routing compatibility mode for extensions’ should be enabled to deny unauthorized users in suspicious actions.
Upgrade PHP and Apache versions
This also contributes to overall Magento security. PHP versions lower than 5.6, that are vulnerable to attacks and no longer have any official support. You can check a vivid graph for currently supported versions, the duration of activity and security support for them. Remember that older unsupported releases are fraught with undiscovered and unfixed security vulnerabilities, and upgrading to supported ones is strongly recommended.
Now to the Apache version you have. If it is older than 2.2, it isn’t completely safe to use, because there is a possible denial of service vulnerability. A determined attacker can take the whole system down using this flaw. Here you can see more details on this issue: Apache 2.2 < 2.2.20 Multiple Vulnerabilities. And there is the only solution: upgrade.
Configure Proper Admin Settings
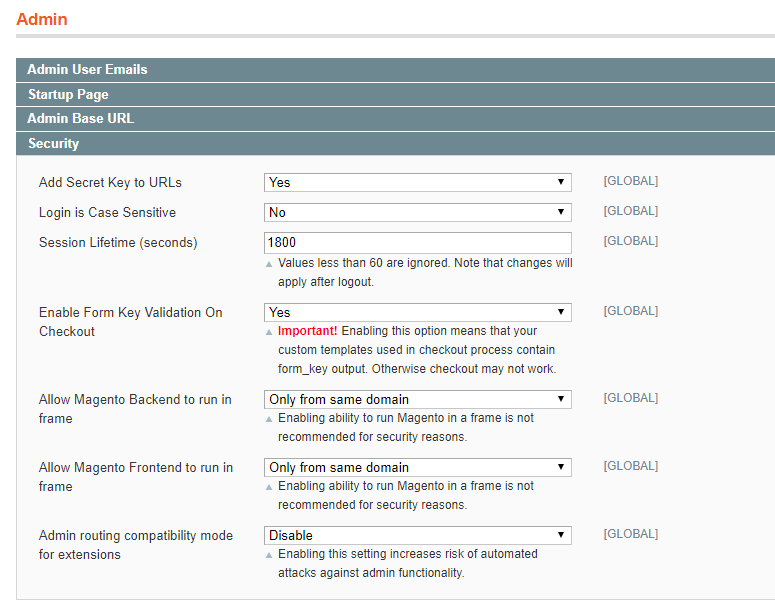
Magento provides admins with extended settings that we already mentioned briefly in the first point. These settings allow to set restrictions that might be very useful when it comes to maintaining the administration process secure. They are located under System > Configuration > Admin > Security. Pay special attention to the following options:
- Add a Secret Key to URLs – if enabled, this option prevents Cross-site request forgery attacks, which exploit the trust a website gives to the user. If disabled, this opens your website up for possible attacks and unauthorized commands.
- Login is Case Sensitive – if enabled, it will provide better security for admin usernames that contain letters in different cases. Therefore, it is preferable to think through more complex admin usernames beforehand.
- Session Lifetime (seconds) – the lowest value you set, the better it is. A lower value means that every admin user has to confirm their identity once in a chosen period of time to continue working in the admin panel.
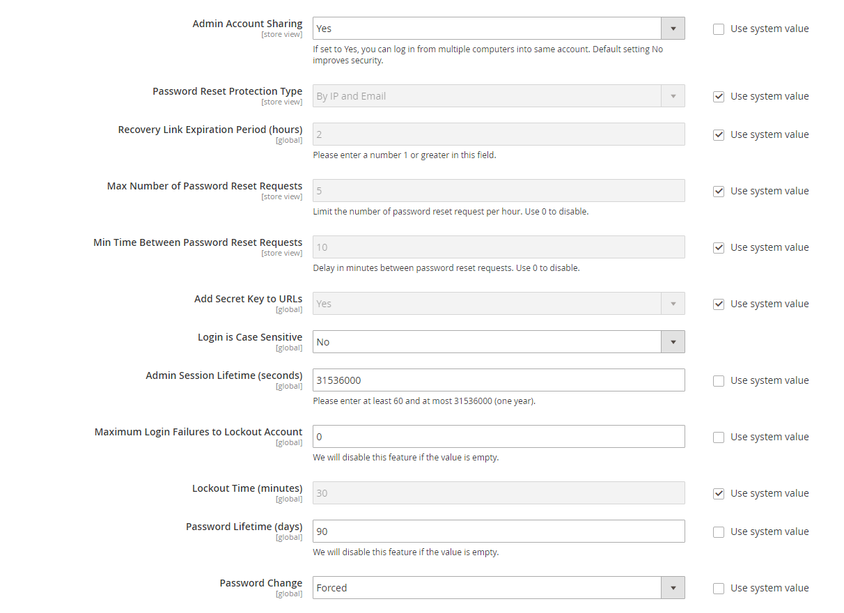
On the screenshots below, the options are set accordingly to the recommendations provided, both for Magento 1 and Magento 2 security.
Admin User Emails
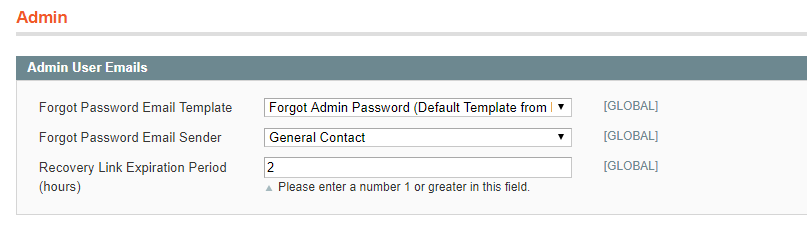
Everytime an admin user forgets their password, they can request a link to recover it. It is extremely important for Magento security to restrict access and lifetime of such a link because once it is in the wrong hands, your business is in danger.
There is a setting for this located under Admin > Admin User Emails.
Admin Base URL
Another way to make intruders’ attempts ineffective is to use a custom admin URL. By default, admin path and URL looks like htp://yourdomain.com/magento/admin. Knowing this path, determined attackers can a malicious script on your website. Changing this URL is not the ultimate solution to script attacks, but it can reduce the chances for a successful break-in. And of course, never expose any valuable credentials.
However, there is a precaution! Do not change the URL and the path in the settings by yourself unless you know how to edit files on the server. Any mistake in the settings can leave you without admin access and can be fixed only in configuration files. If you use a shared hosting, you might also want to check with your hosting provider to make sure your custom URL meets their firewall requirements.
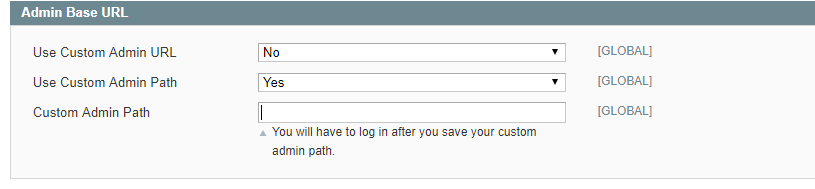
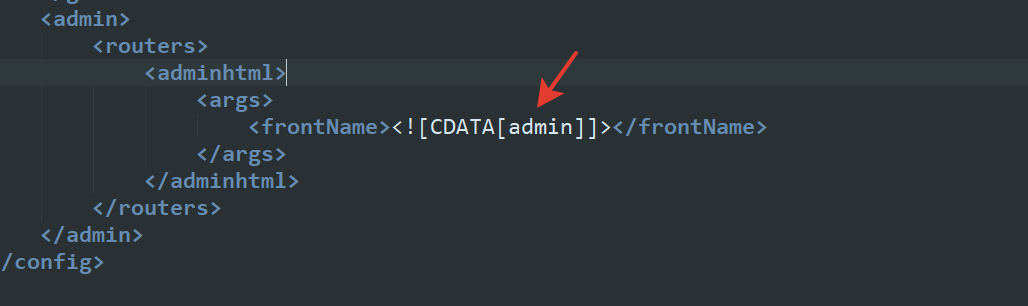
The admin URL can be also changed in app/etc/local.xml file. You should search for <adminhtml> in the <admin> section, change the name to a custom one in [admin] brackets, and then save it.
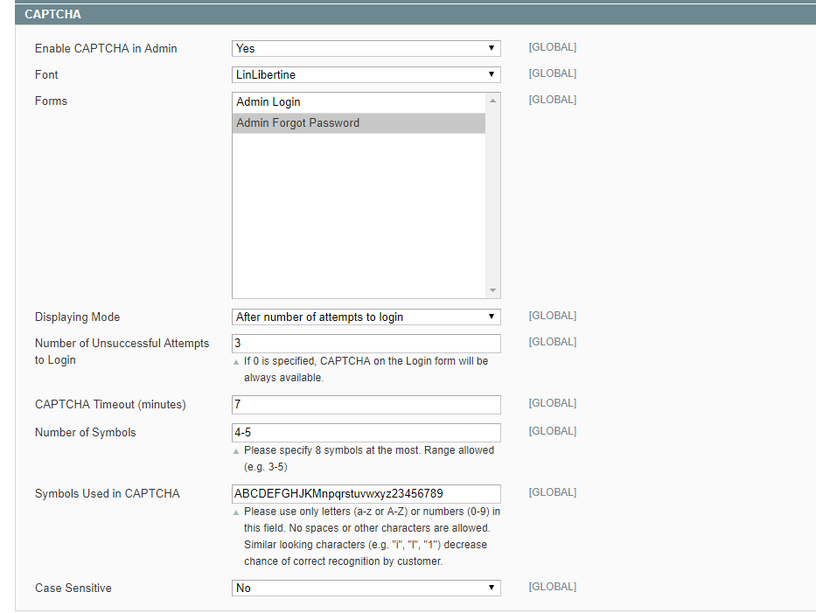
Enable CAPTCHA
Basic Magento functionality offers a wide functionality to protect your website from automated attacks. CAPTCHA settings is another security opportunity for the Magento admin, available both for Magento 1 and 2. Once enabled, CAPTCHA adds another layer of security to the admin panel login page.
To configure CAPTCHA For Magento 1, go to System > Coрnfiguration > Advanced > CAPTCHA. There are no specific recommendations for configuration, however, it is always more secure to set all-time restrictions to minimal possible values.
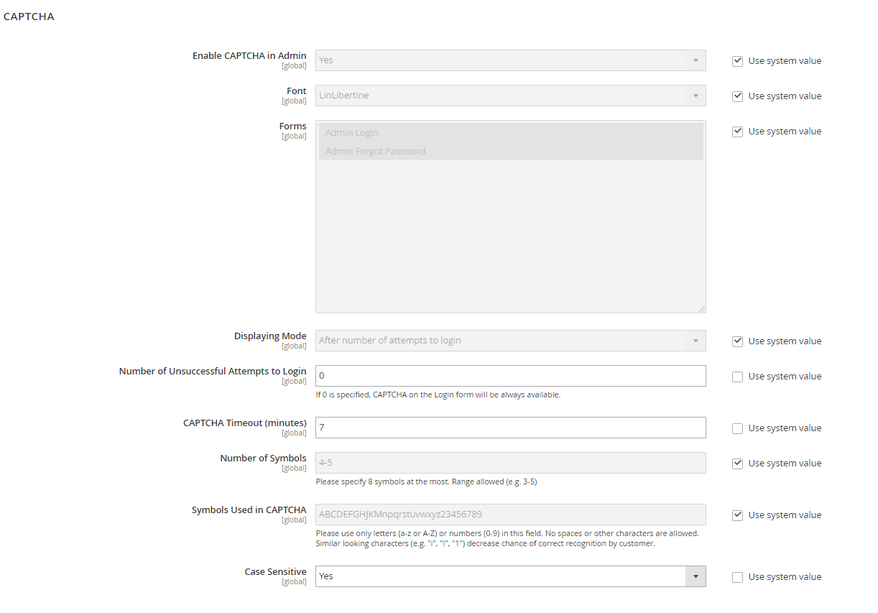
For Magento 2, the path is Stores > Configuration > ADVANCED > CAPTCHA.
Tips for Secure Server Administration
Besides the initial Magento settings, there are other ways Magento administrators can reduce the risks of brute force or attacks. Here is a compact but extensive list of measures that helps in maintaining a Magento security.
- All admin users must undergo a thorough security check before logging in. The best option is to enable two-factor authentication that includes getting a code via SMS.
- Keep all the development, staging and testing systems blocked for outside access. Any leak can be used to sabotage the production system. To control who gets to access and change anything in these systems, configure IP whitelisting and .htaccess password protection.
- Use the correct file permissions for core Magento and directory files, according to Magento recommendations: 755 for directories and 644 for files, and set them to read-only, including app/etc/local.xml files.
- Scripts launching should be forbidden in media and app directories to exclude the possibility to upload and execute a malicious script.
- Set a schedule to execute scanning for viruses once in a specific period of time, for example, once in a few weeks. You can use services like ClamAV and magento-malware-scanner. Before all kinds of scanning, make sure the virus bank is updated to its latest version.
- It is advisable to change the default session_id to something less common to prevent cookies stuffing fraud.
- The access to files with .xml and .json configurations should be blocked on the web server level.
- Make sure you have covered access to the following data:
- app/etc/local.xml
- dev/tests/functional/etc/config.xml
- skin/error.php
- dev/tests/functional/composer.json
- var/resource_config.json
- includes/magmi
- Set the following php.ini parameters to the lowest possible values:
- php_value memory_limit
- php_value max_execution_time
- php_value max_input_vars
- php_value suhosin.post.max_vars
- php_value suhosin.request.max_vars
- php_value upload_max_filesize
- php_value post_max_size
- php_value allow_url_fopen
There are no recommended values for these parameters, though there is a tendency that, the tighter the restrictions are, the harder it is to break in. In this case, the damage the intruders can do to your website will be limited to the time and size restrictions you have already set. For this reason, you need to define the optimized parameters for your online store, depending on the types of content you upload.
Other factors influencing Magento security:
- Never install third-party extensions, especially paid ones, from the sources you can’t trust, like torrents and other sites.
- Always have a recovery plan prepared at hand, and think through the ways you can stop a possible intrusion.
- Make sure your database and servers are backed up automatically to a safe inaccessible location.
What’s Next?
Following the rules mentioned above for Magento security can influence your business positively at any point, whether you are preparing your store to launch or have an established business. However, this is only at the primary stage of equipping your store.
The next one is upgrading to more advanced security measures. But instead of compiling them rigorously from different sources, you can have an all-in-one solution that already contains the tools needed to prevent malicious activity, settings for advanced password policy, admin activity, and has IP Whitelisting and 2FA features included. A complete package comes in the form of Security Suite by NEKLO, an extension for Magento that provides you with extended options for secure store administration. You get full control admin activities, lock user functionality, malware scanning upon request, and many more in a single package.
Author’s Bio
Oksana Mikhalchuk is Content Manager at NEKLO, a software engineering company with a primary focus on ecommerce development for Magento. Oksana is dedicated to writing about marketing, web design and, of course, everything Magento-related.

